IBM Event Streams Quickstart¶
Introduction¶
The instructions in this section will walk you through the steps necessary for setting up a demo environment that can be quickly shown to customers to showcase the art of the possible.
This demo in no way removes the need for following the tutorial style instructions that are documented in other sections of this guide. The instructions below will set up a pre-canned application demo environment to show to the customers.
By the end of this tutorial, you should have a highly available deployment of IBM Event Streams on a Red Hat OpenShift Kubernetes Service on IBM Cloud as shown below.
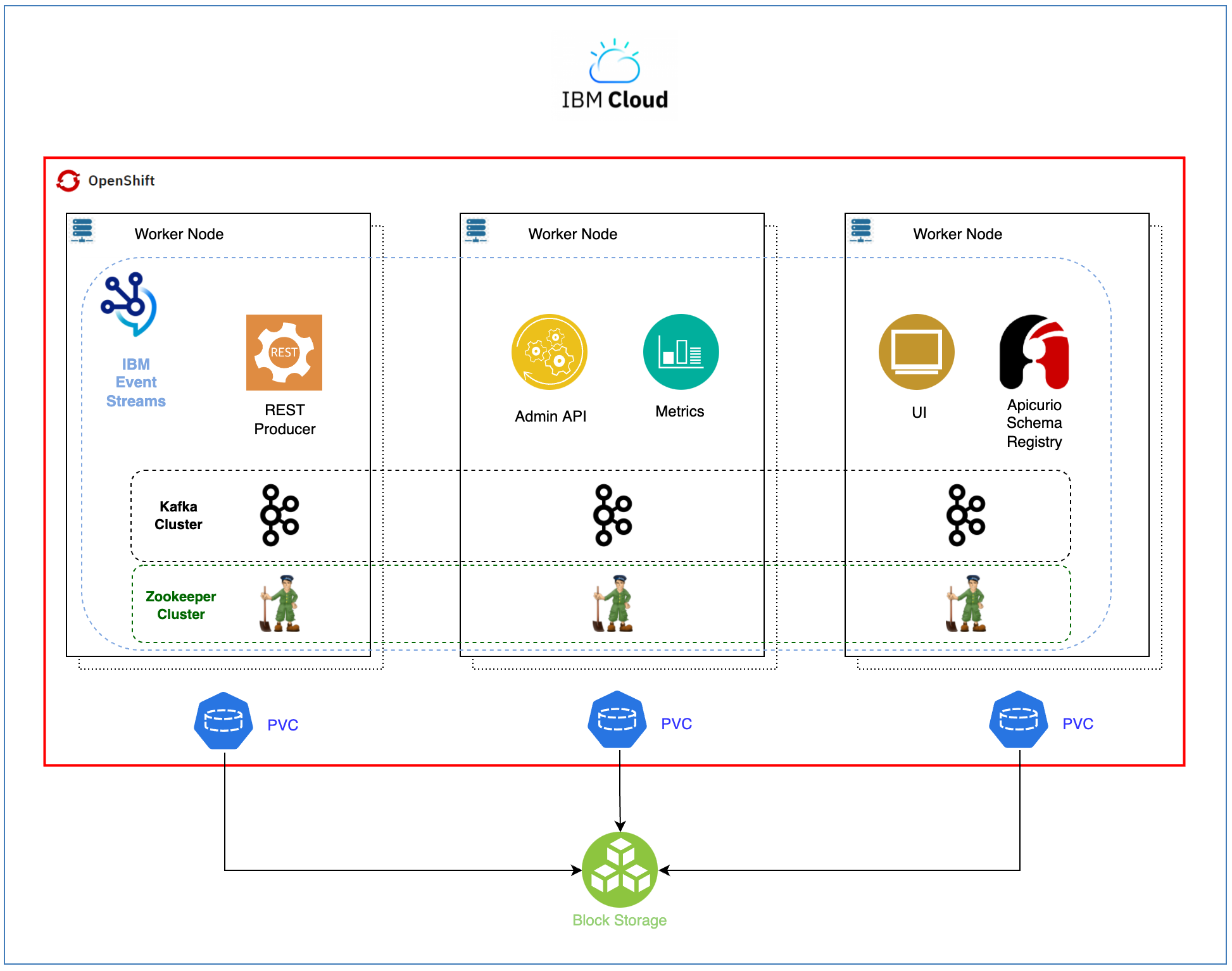
Pre-requisites¶
Create a custom Git Organization¶
Create a new Git Organization to host the different GitOps repositories.
Note
Make sure you do not populate your GitHub organization with cloned repositories. The GitHub organization must be empty and will be populated automatically by the environment provisioning.
Instructions:
-
Log in to http://github.com and select the option to create a New organization.
-
Click on
Create a free organizationplan. -
Complete the wizard by filling in the
Organization account nameandContact emailfields. Select theMy personal accountbullet and complete the verification step and click Next. -
Skip the step to add members to the Organization.
-
Complete the
Welcome to GitHubquestionnaire and click Submit. -
Congratulations, you have successfully created a new Github Organization.
Note
Please ensure your GitHub organization is Public and not Private.
Create a Git Personal Access Token (PAT)¶
Create a new Git Personal Access Token with the appropriate scopes. This will be required to run the application pipelines or to set up webhooks.
Instructions:
-
Log in to http://github.com and click on Settings.
-
Select Developer settings and click on Personal access tokens.
-
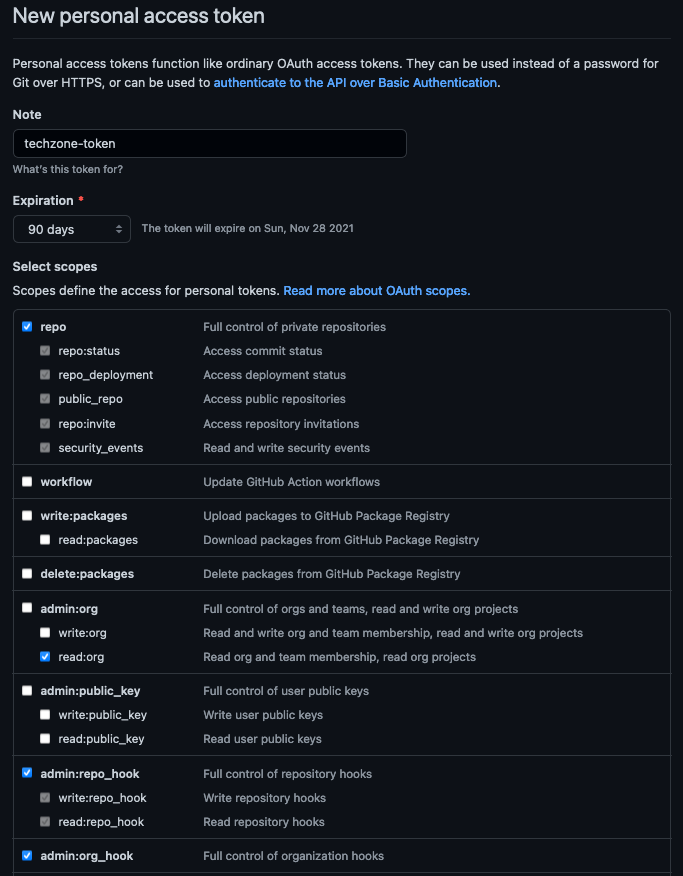
Provide a name for the token, set the
Expirationto 90 days ,set the following scopes and click Generate token.GitHub Personal Access Token scopes
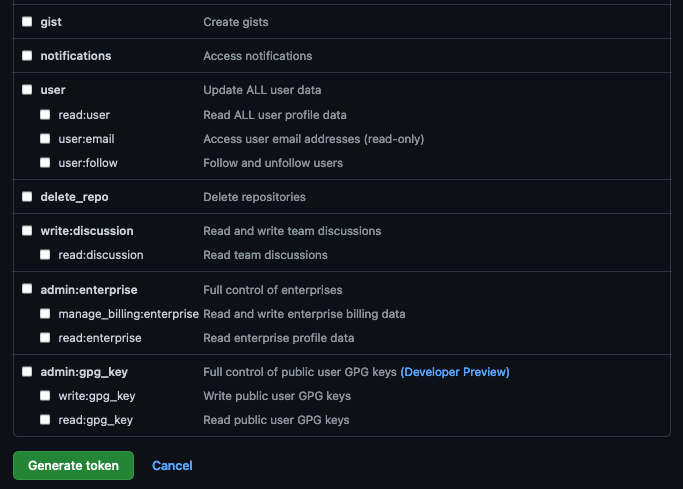
-
Copy and save the Personal Access Token. You will not be able to retrieve this value again later.
Red Hat OpenShift on IBM Cloud cluster with GitOps Configuration¶
Create the cluster¶
-
Provision a Red Hat OpenShift on IBM Cloud cluster with GitOps Configuration from IBM Technology Zone. Select the
OpenShift + GitOps Configurationtile. -
Click the Reserve now radio button.
-
Provide a name for the cluster, select Practice / Self-Education for the purpose and choose the region to provision the cluster.
-
Once a Preferred Geography has been selected, provide the appropriate Worker Node Count and Worker Node Flavor values based on the requirements for this quickstart listed in the note below. Finally, click Submit.
Note
For this IBM Event Streams quickstart we recommend you to request the Red Hat OpenShift on IBM Cloud cluster with GitOps Configuration with the following size:
- Worker Node Count = 3
- Worker Node Flavor = 8 CPU x 32 GB
- NFS Size = 500GB
Use the cluster¶
You will receive an email once the cluster provisioning is complete. The email will contain details on the cluster including the ArgoCD Console URL and admin credentials. This same information can also be found on the My reservations from IBM Technology Zone.
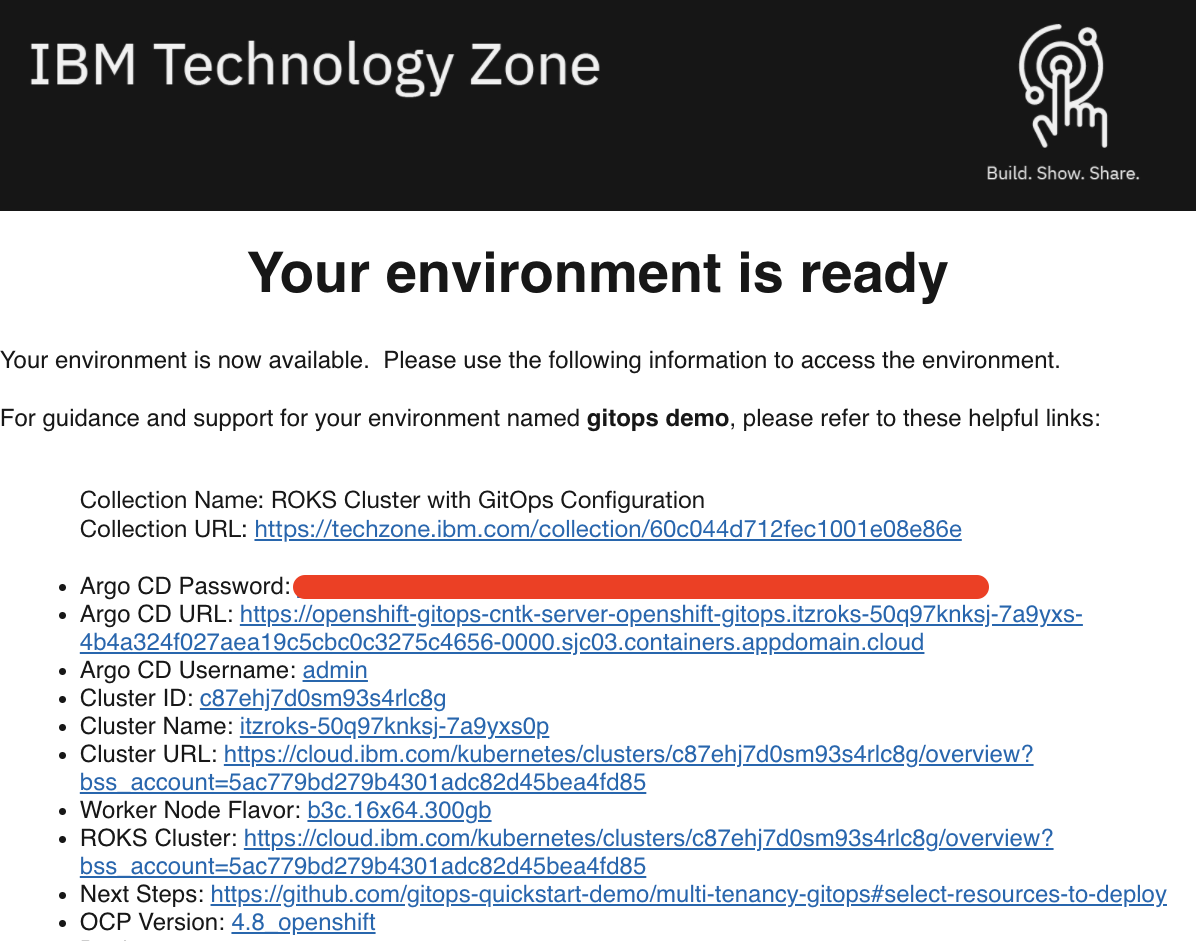
Once your cluster is ready, proceed to the next step to select resources to deploy.
Install required CLIs¶
- Install the Github CLI (version 1.14.0+)
-
Install the OpenShift CLI
oc(version 4.7 or 4.8)-
Log into your OCP cluster, substituting the
--tokenand--serverparameters with your values:oc login --token=<token> --server=<server>If you are unsure of these values, click your user ID in the OpenShift web console and select
Copy login command.
-
-
Install the kubeseal CLI
The kubeseal utility uses asymmetric crypto to encrypt secrets that only the controller can decrypt. These encrypted secrets are encoded in a SealedSecret resource which can safely be checked into your gitops repo. The controller will decrypt the secretes and install into your cluster.
Select resources to deploy¶
By now, you should already have a Red Hat OpenShift on IBM Cloud cluster with GitOps Configuration bootstrapped for you.
If you open ArgoCD, which is the GitOps tool being installed by the Red Hat OpenShift GitOps Operator, using the Argo CD URL provided in the email shown in the previous section, you will see that your ArgoCD GitOps application has been bootstrapped to monitor the multi-tenancy-gitops repository that has been forked into the GitHub organization you provided when requesting the quickstart environment.
As a result, anything you want to apply/do to your quickstart environment will be done through code changes on the aforementioned forked GitHub repository.
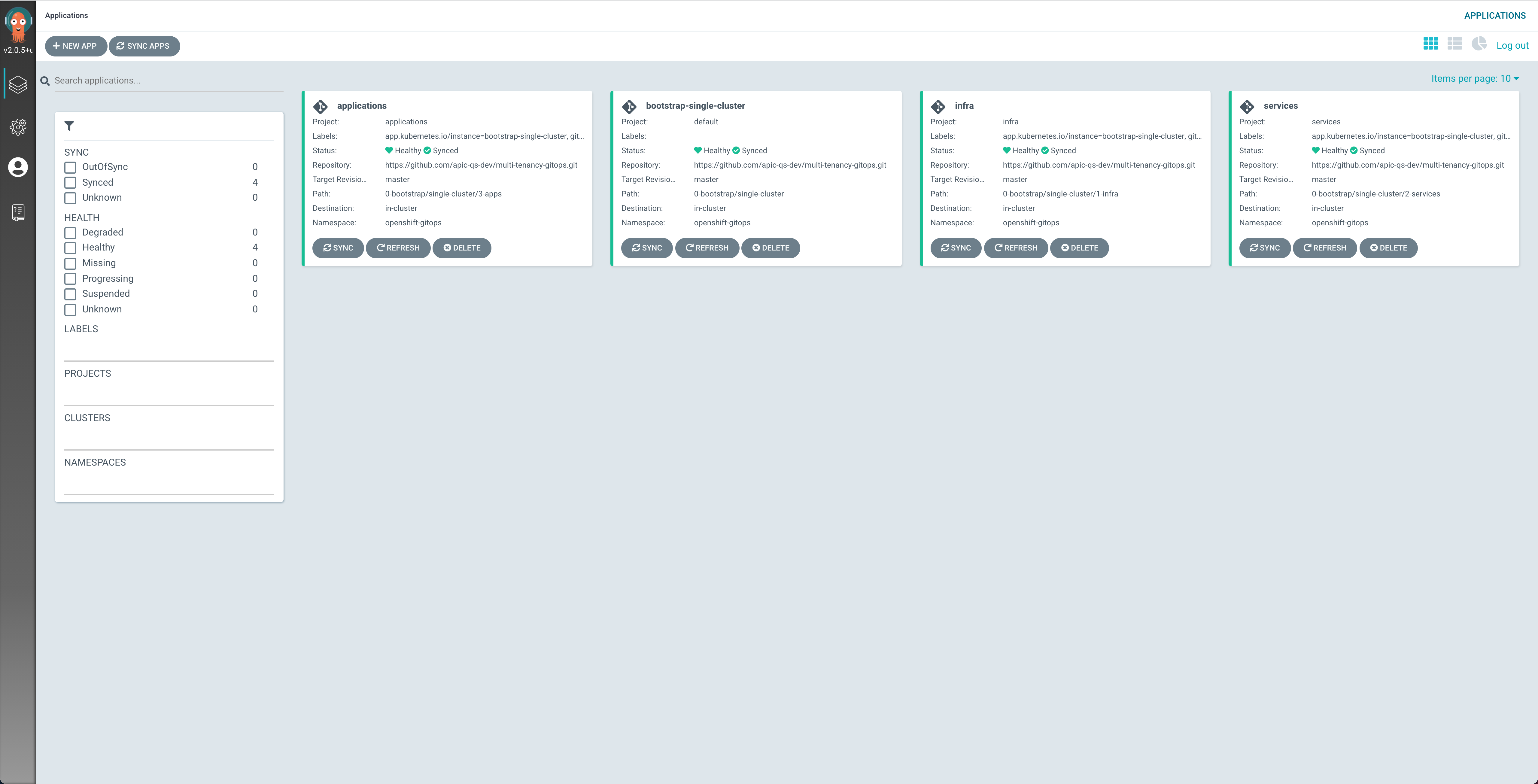
You can see in the image above of your ArgoCD web console that the profile within the multi-tenancy-gitops repository ArgoCD has been bootstrapped with is the single-cluster. As a result, anything you want to apply/do to your quickstart environment will be done within that GitOps profile.
You can also see that the ArgoCD applications for the infrastructure, services and applications layers are already created so that these will pick up any changes done, through code, at their respective layers.
Instructions¶
-
You can execute the following steps either locally by cloning the
multi-tenancy-gitopsGitHub repository the IBM Technology Zone environment request automation has forked into the GitHub organization you created in the Pre-requisites section above for you to your local workstation (then make changes from your local workstation and commit and deliver those to GitHub) or by using the new VSCode extension of GitHub Codespaces capability straight from your web browser (just open themulti-tenancy-gitopsrepository in your Git Organization in your browser and press the.key):- Review the
Infrastructurelayer kustomization.yaml and un-comment the resources to deploy to match the IBM Event Streams recipe. - Review the
Serviceslayer kustomization.yaml and un-comment the resources to deploy to match the IBM Event Streams recipe. - Review the
storage,high availabilityandsecurityoptions for the IBM Event Streams instance definition explained in the IBM Event Streams recipe. - Commit and push changes to your git repository (the following code refers to the commands when you cloned the
multi-tenancy-gitopsrepository locally on your workstation)git add . git commit -m "initial bootstrap setup" git push origin
- Review the
-
After some time, you can validate your new instance of IBM Event Streams is ready by executing:
Expected output isoc get eventstreams -n toolsNAME STATUS es-inst Ready -
You can now access your IBM Event Streams User Interface
oc get EventStreams es-inst -n tools -o=jsonpath='{.status.endpoints[?(@.name=="ui")].uri}' -
The credentials for logging into the IBM Event Streams User Interface are
admin/<password>where password is stored in a secret.oc get secret platform-auth-idp-credentials -n ibm-common-services -o=jsonpath='{.data.admin_password}' | base64 -D